Security at a Breaking Point: Why the SOC Stack Must Evolve
The volume, complexity, and velocity of modern threats are overwhelming security teams.
Here’s what the future of AI-powered SOCs needs to look like.
The digital security landscape is evolving, and Security Operations Centers (SOCs) are under increasing strain. While AI has strengthened defense strategies, it’s also enabled attackers to move faster and smarter, forcing SOCs to keep pace with an ever-changing threat environment.
SOCs now handle around ~4,500 alerts per day. And 67% of those daily alerts never get investigated, not because they aren’t important, but because the sheer volume makes it difficult to investigate them all. Tools like SIEM, SOAR, and EDR—intended to streamline security—often add complexity instead, generating excessive false positives or failing to prioritize the most urgent threats. As a result, real risks can get buried in the noise.
And those risks? They’re advancing fast. AI-powered attacks, like automated phishing and smarter malware, are quickly becoming the norm. In security, response time is everything – even short delays can give attackers the upper hand. That’s why reducing the Mean Time to Respond (MTTR) is now a non-negotiable for modern SOCs.
Meanwhile, enterprises’ environments are expanding. They’re no longer just monitoring a handful of systems: SOCs are managing logs from a plethora of assets across endpoints, servers, cloud platforms, and individual security applications. Each system often speaks its own language and outputs unique data formats, generating massive amounts of disparate data SOC teams must decipher and string together into logical events.
Without standardization and with ever-increasing tool sprawl, SOC teams lose valuable time just making sense of existing data, before they can act on it.
Add to that the well-documented talent shortage, and the challenge grows steeper. With experienced security professionals in short supply, teams are stretched thin, workflows become outdated, and critical alerts risk being overlooked. While automation has helped in some areas, many solutions still require heavy manual intervention—and without AI, truly effective automation remains out of reach.
Despite broader market volatility and economic uncertainty, AI spending shows no signs of slowing. As the Wall Street Journal reported recently, Big Tech is holding firm on AI investments—Google is maintaining a $75 billion AI budget, and Amazon’s CEO called AI a “once-in-a-lifetime reinvention of everything we know.” This confidence reflects what we’re seeing in enterprise security: even amid cost pressure, CISOs and boards appear committed to funding modernization—especially projects that reduce manual overhead, address alert fatigue, and create measurable ROI through AI-native tooling.
How SOC Works – The Good, The Bad, The Way Forward
The Good:
Today, most SOCs are characterized by a 3-tiered model, correlating to severity and complexity of alerts:
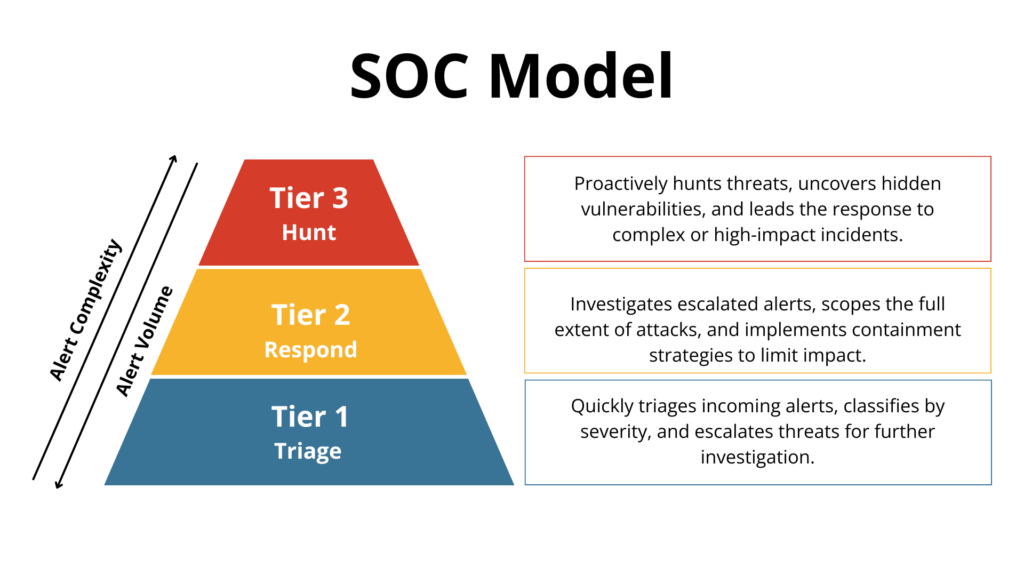
Employees across these teams rely on a variety of tools to detect and respond to threats. For the sake of simplicity, let’s narrow the core configuration to three layers: event data, analytics, and response. Event data includes everything from endpoint logs to cloud alerts; the analytics layer is where signals are correlated and prioritized; and the response layer initiates actions to contain threats.
The Bad:
As we highlighted earlier, relevant log data comes from a multitude of individual tools, and is often one of the largest data sets by volume in an enterprise. While each of these tools are effective at seeing what’s happening – by detecting and flagging suspicious anomalies at the asset-level – they don’t see what it means in context of the broader system. Said another way, they don’t connect the dots. That means it’s up to SOC team members to use analytics tools to manually piece together these signals into a coherent incident and assess how serious the potential downstream impact might be.
This analysis usually happens on top of a central visibility layer, where the data flows into – most commonly a SIEM (Security Information and Event Management) system. SIEMs aggregate, normalize and analyze security data from across the organization to detect threats and provide real-time visibility. But that visibility comes at a cost: SIEMs require significant implementation and ongoing maintenance to ingest data from fragmented sources with varying formats.
Engineering effective detection logic often means writing complex rules in vendor-specific query languages like Splunk’s SPL, which come with a steep learning curve. Integrating new data sources can be rigid and slow, and the cost of operating SIEMs – driven by data ingestion, storage, and the compute required to run frequent queries and analytics to effectively understand alerts – can quickly balloon as environments grow.
To cope with these challenges, many organizations now run multi-SIEM environments or pair SIEMs with Security Data Lakes or Pre-processing tools to enhance their analytical capabilities. A recent report by Cribl found that the number of customers sending data to multiple SIEM platforms has grown 45% year-over-year. This patchwork approach, while more powerful, adds complexity and management overhead.
At the end of the day, a SIEM is only as effective as the ongoing effort behind it and in today’s advanced attack environment, the effort required is often too much to maintain.
The final layer is response – typically powered by SOAR (Security Orchestration, Automation, and Response) tools. SOARs are built to prioritize and automate incident responses by pulling in alerts from SIEMs and triggering pre-defined remediation workflows.
But these workflows are based on rigid “if-this-then-that” logic. If an attack doesn’t follow a predetermined pattern, the system can fail to respond effectively. That leaves analysts constantly updating playbooks to keep up with evolving threats, ironically turning what was meant to be an automation tool into yet another manual task.
On top of that, SOAR tools often struggle to integrate with the growing sprawl of security solutions, making it hard to maintain a cohesive, end-to-end response strategy. The result is a tool that demands heavy customization, drives up total cost of ownership, and still falls short of its original promise. What we need now is automation that can learn and adapt, not just follow a script.
Despite their importance, today’s SOC tools rely heavily on manual effort. Each tool is built for a specific layer, but stitching them together manually is left to the security team. In many cases, alerts pass through six to eight systems before they even reach a human analyst! That means valuable time is lost to correlating signals, adjusting detection rules, and updating automation logic. But it’s important to call out that even in a world of perfect tooling, so much of the SOC’s ability to be effective relies on infusing the tribal knowledge of experienced analysts into the process.
The Way Forward:
That’s where LLMs and advancements in AI come in. An AI-powered SOC offers a critical set of capabilities that can help reduce the amount of time spent toggling between disparate tools and manually analyzing events – allowing them to focus on what humans are best at: infusing undocumented context. Specifically, modernized tools can provide:
- Deep contextual understanding – By correlating multiple data signals and continuously incorporating and learning from feedback from humans, AI-based platforms ensure critical insights and tribal knowledge remain readily accessible.
- Proactive Security Intelligence – AI-powered SOC solutions move beyond reactive incident response by continuously monitoring weak spots, code bases, and security posture changes, informed by deep pattern recognition and contextual understanding, recommending actions that mitigate threats before they escalate.
- Seamless data integration – LLMs excel at ingesting and normalizing data from a wide range of sources – logs, vulnerability scans, identity tools, and more – creating a unified and coherent view of an organization’s risk profile.
- Improved detection capabilities – For technical teams, the rise of “Detection as Code” is being enhanced by AI-coding tools like GitHub Copilot that help engineers maintain a more adaptive rule base, something historically too resource intensive. Meanwhile, natural language interfaces empower non-technical anlaysts to easily run queries and respond to alerts without extensive training.
The true power of AI in the SOC lies in a unique combination: the intuitive understanding of Large Language Models (LLMs) paired with the strategic decision-making of AI Planning. LLMs help decipher the chaos, summarizing alerts and generating rapid insights, while AI Planning connects the dots, mapping attack chains and automating dynamic, multi-step responses in a way that static rules simply can’t.
As one Forrester analyst put it: “We are at this inflection point.” And with security software projected to grow from $59.9B in 2022 to $134.3B by 2028, AI-native platforms aren’t just a nice-to-have—they’re central to how security leaders are planning for the future.
This isn’t just an upgrade – it’s a fundamental shift.
As security threats accelerate and grow more sophisticated, so must our defenses. And it doesn’t stop with AI-powered SOC solutions. The friction points outlined make way for a broader rethinking of the existing security stack – whether the unbundling of Splunk or securing new attack vectors, we’re actively investing in the founders building this next generation of security infrastructure. If you’re rethinking how SOCs operate, I want to speak with you.
This article is for informational purposes only and does not constitute investment advice. Saaya Pal is a Partner at Jump Capital. Rahul Manchanda contributed to this article during his internship at Jump Capital. Views expressed represent the opinions of the authors and Jump Capital. Jump Capital may have investments in or pursue investments in the technology sectors and companies discussed. Market projections are based on third-party research and are not guarantees of future outcomes. References to specific companies do not constitute investment recommendations.


 Front Page
Front Page